How Does a Firewall Work? A Beginner’s Guide to Network Security

How Does a Firewall Work? A Beginner’s Guide to Network Security
Introduction:
In our increasingly connected world, securing sensitive information and ensuring secure communication is more critical than ever. One of the core components in the cybersecurity toolkit is the firewall. A firewall serves as the first barrier between your internal network and external threats, monitoring incoming and outgoing traffic. But what exactly does it do, and how does it protect you? Let’s break down the fundamentals of how firewalls operate, their vital role in shielding against cyber-attacks, and why they are essential for maintaining a secure network environment.
What Is a Firewall?
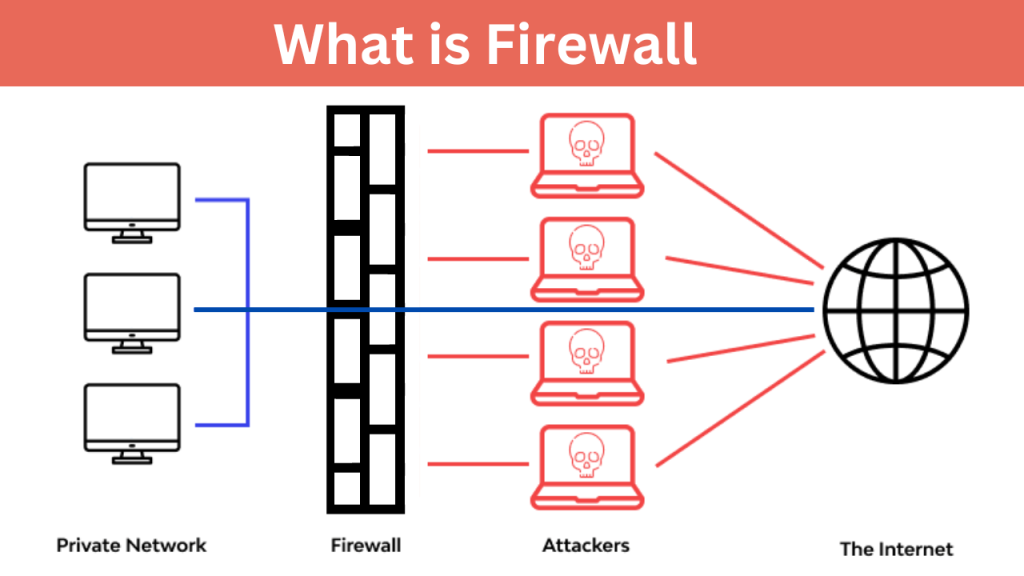
A firewall is a vital network security system that monitors and controls traffic flow between a trusted internal network and external networks, like the internet, based on predefined security rules. It acts as a gatekeeper, blocking unauthorized access and potentially harmful data while allowing legitimate communications to pass through. Operating as a filter, it evaluates data packets and enforces security policies set by the network administrator. Firewalls can be implemented as software, hardware, or a hybrid solution, providing protection at various levels of a network to shield against cyber threats.
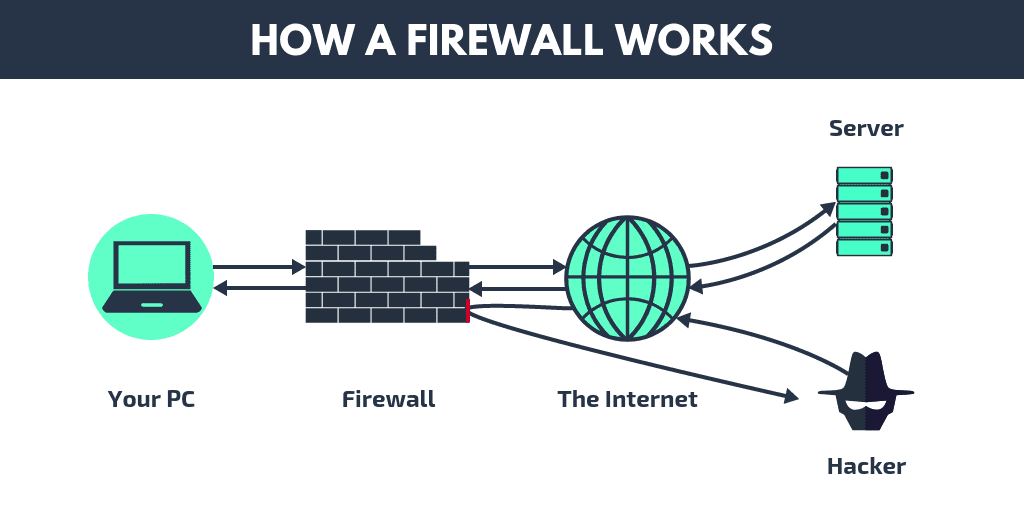
How Does a Firewall Work?
A firewall is a critical component in network security, functioning as a gateway that controls the flow of data between a trusted internal network and untrusted external environments, such as the internet. It operates by enforcing predefined security policies, which determine how network traffic should be handled. Firewalls analyze individual data packets, examining key information like source and destination IP addresses, port numbers, protocol types (e.g., TCP, UDP), and packet flags. Depending on the configuration, they can either allow, block, or reroute traffic based on these attributes. The process varies depending on the type of firewall, but here’s a breakdown of how they generally function:
- Packet-Filtering Firewalls: Packet-filtering firewalls are a basic security tool that inspects individual data packets based on predefined rules, such as source and destination IP addresses, protocols (e.g., TCP, UDP), and port numbers (e.g., HTTP on port 80). They determine whether to allow or block traffic by evaluating these criteria, providing essential control over network access.
- Proxy Firewalls : Proxy firewalls act as intermediaries between users and the internet, filtering traffic at the application level. They inspect requests and responses, ensuring harmful content is blocked before reaching the internal network, providing enhanced security and privacy.
- Deep Packet Inspection (DPI): Modern firewalls use Deep Packet Inspection (DPI) to examine both packet headers and the data content. This helps detect and block hidden threats like malware and advanced attacks that might evade traditional security measures. DPI provides a more thorough and effective layer of protection by analyzing the full content of network traffic.
Types of Firewalls
There are several types of firewalls, each suited for different network environments and security needs:
Network Firewall : These firewalls are typically deployed at the network’s perimeter to protect the entire infrastructure. They monitor and control traffic between an internal network and external sources. Network firewalls come in two forms:
- Hardware Firewalls: These are dedicated physical devices placed between the network and the external world. They are ideal for protecting entire networks from external threats.
- Software Firewalls: Installed on individual devices, these firewalls protect specific systems from both internal and external threats.
Next-Generation Firewalls (NGFWs) : NGFWs are more advanced than traditional firewalls, integrating features like:
- Intrusion Prevention Systems (IPS): Detects and blocks malicious activities.
- Application Awareness: Inspects traffic at the application level to enforce security policies.
- Advanced Threat Detection: Identifies more complex threats, such as malware or zero-day attacks.
Cloud Firewalls : With the rise of cloud computing, cloud firewalls have become essential. These virtual firewalls are designed to protect cloud-based infrastructure and applications. They monitor traffic between cloud services and users, ensuring security in dynamic cloud environments.
Web Application Firewalls (WAFs): WAFs protect web applications by filtering and monitoring HTTP/HTTPS traffic. They are specifically designed to defend against web-based attacks such as SQL injection, cross-site scripting (XSS), and other vulnerabilities that target online services.
Unified Threat Management (UTM) Firewalls:UTMs combine multiple security features, such as antivirus protection, intrusion detection, and content filtering, into a single solution. They are ideal for small and medium-sized businesses looking for comprehensive protection in one package.
Key Firewall Features
Modern firewalls offer a variety of features to enhance security:
- Access Control: Firewalls allow administrators to define who can access specific resources, services, or applications. Granular access control ensures that sensitive areas of the network are protected from unauthorized users.
- Logging and Monitoring: Firewalls keep detailed logs of all network activity. These logs are invaluable for security audits, detecting anomalies, and identifying potential security breaches.
- Content Filtering: Firewalls can filter web content, blocking access to sites that are known to distribute malware or inappropriate material. This is commonly used in corporate environments to prevent employees from accessing malicious or distracting content.
- Routing and Switching: Routing directs network packets from source to destination via protocols like OSPF and BGP, ensuring efficient data flow and secure connectivity. Switching forwards data within networks to their destinations, enabling seamless communication. Understanding both is crucial for designing robust network architectures.
- Intrusion Detection and Prevention: Many firewalls now come equipped with intrusion detection and prevention systems (IDPS) that monitor network traffic for suspicious activity and automatically block potential threats.
- Threat Intelligence Integration:Some firewalls are integrated with threat intelligence platforms that provide real-time updates on known threats, enabling firewalls to block new attacks as they emerge.
Conclusion:
Firewalls are vital for protecting against cyber threats, ensuring secure data flow and blocking malicious traffic. Whether for personal or enterprise use, a well-configured firewall is essential in defending networks. In today’s digital world, mastering firewall deployment is crucial for maintaining a strong defense against evolving cyberattacks.



